Quick Steps to Import a Root CA on Ubuntu
1. Ensure the certificate is in PEM format and has a .crt extension.
2. Copy the certificate to /usr/local/share/ca-certificates/.
3. Run the update command:
sudo update-ca-certificates
Debugging Certificate and Signature Issues with OpenSSL
OpenSSL is a powerful tool for working with certificates and signatures.
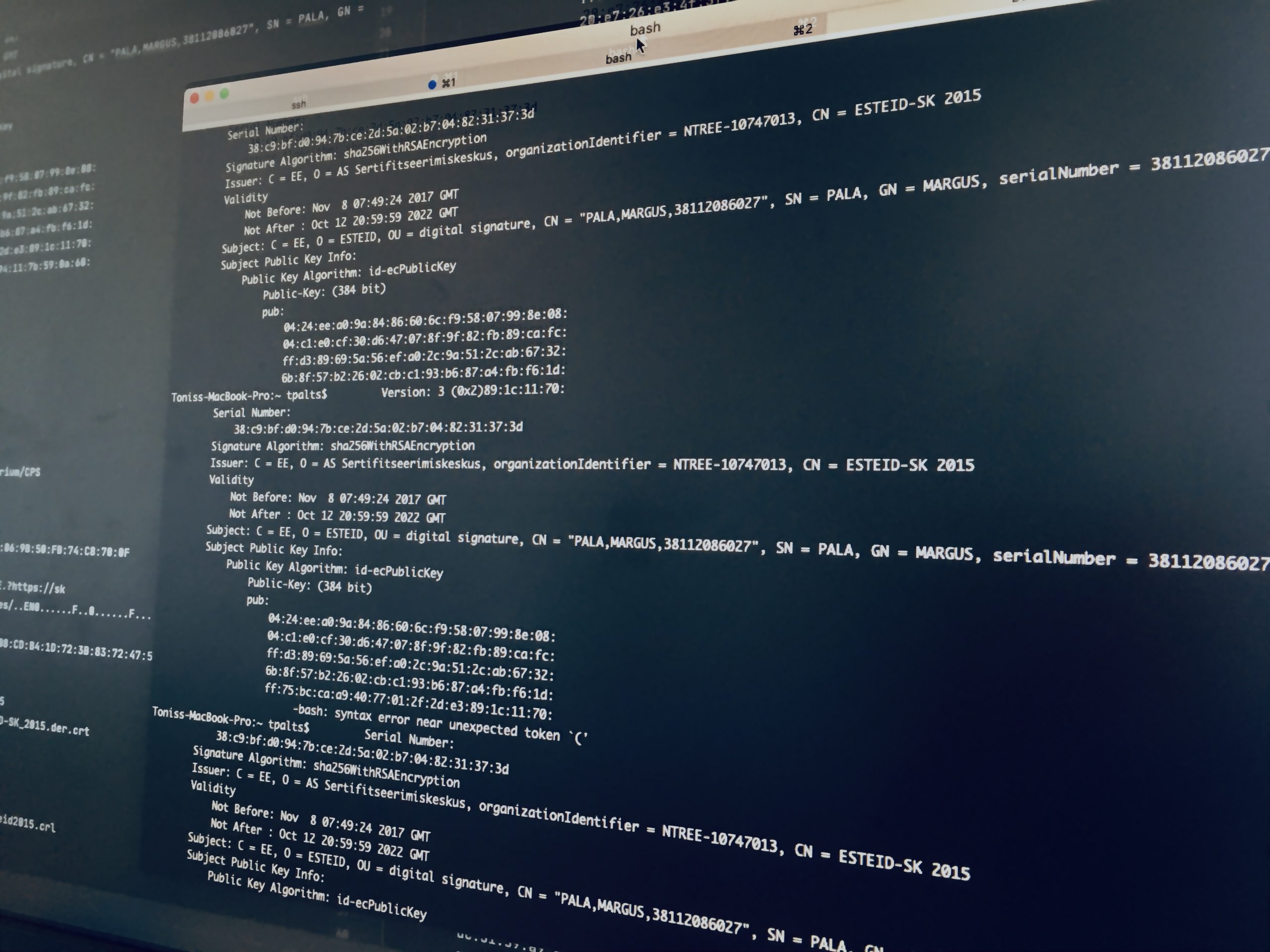
For example, verifying a certificate might fail if the issuer’s CA certificate is missing:
$ openssl verify 38112086027.cer
error 20 at 0 depth lookup: unable to get local issuer certificate
error 38112086027.cer: verification failed
This means the signing (issuer) certificate is missing from the trust store.
How to Resolve This
Step 1: Inspect the Certificate
Use OpenSSL to examine the signer certificate:
$ openssl x509 -in 38112086027.cer -text -noout
Key fields:
- Issuer:
C = EE, O = AS Sertifitseerimiskeskus, CN = ESTEID-SK 2015 - Authority Information Access:
- CA Issuers URL:
http://c.sk.ee/ESTEID-SK_2015.der.crt
- CA Issuers URL:
This points to the ESTEID-SK 2015 intermediate CA certificate.
Step 2: Download and Convert the Issuer Certificate
1. Download ESTEID-SK_2015.der.crt from the provided URL.
2. Convert it to PEM format:
$ openssl x509 -in ESTEID-SK_2015.der.crt -inform der -out ESTEID-SK_2015.pem.crt
Step 3: Verify the Chain
Check if verification succeeds using the issuer certificate:
$ openssl verify -CAfile ESTEID-SK_2015.pem.crt 38112086027.cer
38112086027.cer: OK
Step 4: Add the CA Certificate to Ubuntu Trust Store
Copy the PEM certificate:
$ sudo cp ESTEID-SK_2015.pem.crt /usr/local/share/ca-certificates/
Update the trust store:
$ sudo update-ca-certificates
Result:
- Certificates are added under
/etc/ssl/certs/. - OpenSSL now trusts signatures from this CA.
Verification:
$ openssl verify 38112086027.cer
38112086027.cer: OK
Potential Issues and Troubleshooting
1. OpenSSL Version Problems
Different Ubuntu versions may have different OpenSSL behaviors:
- Ubuntu 18.04: OpenSSL 1.1.1
- Ubuntu 20.04: OpenSSL 1.1.1f (known bugs)
Upgrading from OpenSSL 1.1.1e/f may cause issues with SSL connections (e.g., OpenVPN). In some cases, compiling a newer OpenSSL (e.g., 1.1.1g) manually may help but doesn't solve all problems.
Reference: GitHub Issue #11456
2. Certificate Permissions Issue
Newly added certificates might lack read permissions, leading to OpenSSL errors like:
Permission denied: fopen('/usr/lib/ssl/certs/xxxxx.0','r')
Solution: Set read permissions manually:
$ sudo chmod +r /usr/local/share/ca-certificates/ESTEID-SK_2015.pem.crt
Final Notes
- The root CA for Estonian ID cards (EE Certification Centre Root CA) is usually already installed on Ubuntu.
- Only intermediate CAs like ESTEID-SK 2015 may need manual installation.
By following these steps, you can properly trust and verify Estonian digital signatures or any other PKI-based certificates.